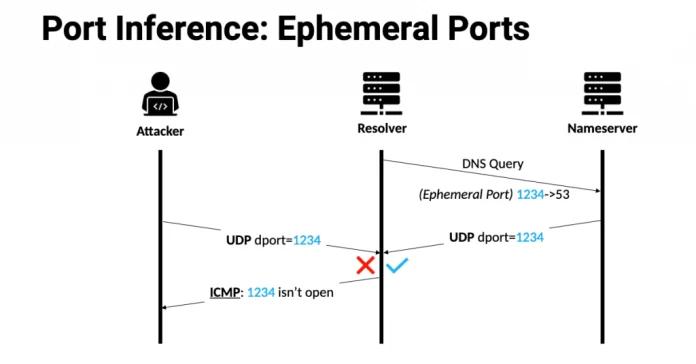
A temporary port is also referred to as an ephemeral port; it refers to a short-lived IP communications However, Temporal ports there be multiset provision from disparate IP stacking software that incorporate temporary ports. When two networks communicate through some of the most recognized port names such as Transmission Control Protocol (TCP), User Datagram Protocol (UDP), or Stream Control Transport Protocol (SCTP). Ephemeral ports allow communication passages to be established between the clients and server devices by their unique identifiers assigned for each network session. The address of this identifier is referred to as a socket and links the IP addresses and port numbers of client, server device.
When a client service initiates a connection with a service server on the network, the operating system assigns a temporary port number to the client specifically for this communication. This temporary port acts as the final client to send data to and receive data from the server. Once the negotiation is complete, the temporary port is released back into the pool of available ports for reuse.
How do temporary ports work?
Although temporary ports are generally associated with client communications, the server also plays a role in managing temporary ports in the event of an outage. Here’s how ad hoc ports work on the server side:
Listening on well-known ports:
Clients typically listen for connections on well-known ports, such as port 80 for HTTP, or use Port 443 for HTTPS. These ports are reserved for specific services, and server services (for example, web servers) are designed to handle requests from these ports.
Accept connection: .
When the client initiates a connection request, the server accepts the connection from the port. A well-known port designed for a specific service. For example, a web server accepts HTTP requests from port 80.
Dynamic allocation of temporary ports:
After the connection is established, the server assigns the incoming connection to be paused for the duration of the session. This temporary port acts as the server’s endpoint to communicate with a specific client during a session.
Data exchange:
The server sends data packets to the client and receives data packets from the client through a temporary port. This communication enables the server to respond to requests, process data, and perform services such as serving web pages, managing database queries, or maintaining data transfer.
Connection terminated:
When the connection terminates (either because the client terminates the connection or the server completes the requested operation), the server releases temporary ports associated with specific user connections. This allows the port to be reused for future connections.
Management:
The server manages a temporary port to manage multiple connections from different clients. By dynamically allocating and releasing temporary ports as needed, the server can utilise available network resources and manage multiple connections.
Why are temporary ports important? Are they safe?
Ad-hoc ports play an important role in optimising network resource allocation. By dynamically allocating ports as needed, the operating system can handle large numbers of connections without available ports. This dynamic distribution also increases security by reducing port numbers and makes it harder for malicious actors to target a specific target.
These ports allow multiple simultaneous network sessions to occur on the same client by assigning a temporary and unique identifier to each network session.
The temporary port itself is not secure. However, they can be used for some types of network attacks, such as port scanning, which involves opening network ports to detect vulnerabilities.
To reduce the risk of attacks against networks that use ephemeral ports, network administrators can set up firewalls and other security measures to block access to ephemeral ports and restricted connections to trusted websites.
Temporary Port Forwarding, Exhaustion and Mitigation
When you use Secure Network Address Translation (SNAT) for clients to initiate (run) connections, the port will be temporarily depleted, possibly depleted It causes SNAT to be unable to handle more traffic to the root. Reconnect the port. BIG-IP can configure your system to detect real-time port and error data and provide Simple Network Management Protocol (SNMP) notifications when the threshold is exceeded, allowing you to identify the port that will appear periodically and act accordingly.
When setting the port order, you can open the port order, specify the initial level, and specify the processing time in seconds.
A weak port can cause poor performance or even no service as the system tries to establish new connections. To mitigate this problem, administrators can do several things:
Fix the operating system failure: Temporarily adjusting the operating system configuration regarding port allocation and recycling can help reduce port throttling. This may include increasing the maximum number of ports available or optimizing the recycling process.
Enable connection reuse: The system can reuse existing connections whenever possible instead of creating new connections for each operation. Convergence technology can help reduce the need for temporary ports by preserving the available connection pool.
Speed Limiting: Applying rate limiting can help control the speed of new connections being established, thus reducing the chance of a port expiring. Traffic or protest. Expanding resources: Expanding infrastructure resources, such as adding servers or increasing network capacity, can disperse connections and reduce the impact of temporary ports.
Conclusion
In summary, the effect of the ad-hoc port is poor networking of all ports, silent exchange of information between devices. Understanding their role and importance is important for anyone involved in network management or development. By recognizing the importance of temporary ports and implementing appropriate mitigation strategies, organisations can increase the reliability, security, and efficiency of their systems.